Vulnerability report :
Any potential vulnerability that may be identified must be communicated to BUBENDORFF by means of a Report sent to via the form at the bottom of the page.
The User is asked to indicate in his Report:
Details of vulnerability (mandatory)
. Title of vulnerability ;
. Medium (internet address, IP address, product or service name, S/N number – mandatory if the medium is a product) where the vulnerability has been/can be observed ;
. Estimated severity, assessed according to the Common Vulnerability Scoring System (CVSS 3.0) :
. Description of vulnerability (including summary, justification and any proposed mitigation measures or recommendations) ;
. Impact (what an attacker could do with this vulnerability) ;
. Steps to be taken to reproduce the vulnerability. This must be a benign and non-destructive proof of concept. This ensures that the report can be processed quickly and accurately. It also reduces the likelihood of duplicate reports or malicious exploitation of certain vulnerabilities, such as subdomain takeovers.
User contact information (mandatory)
. User name
. User’s e-mail address
Report processing :
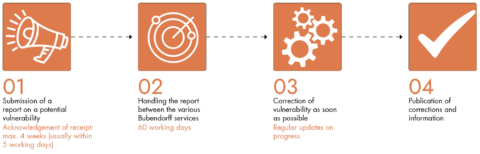
BUBENDORFF acknowledges receipt of the report within a maximum of 4 weeks (usually within 5 working days) of its receipt. The report is handled by the BUBENDORFF teams who will make their best efforts to carry out the Vulnerability Treatment within a maximum of 60 working days following the acknowledgement of receipt. BUBENDORFF will endeavour to keep the User informed of its progress.
The priority of corrective actions is assessed according to the impact, seriousness and complexity of the vulnerability. The vulnerability may take some time to be corrected. BUBENDORFF may also contact the User by e-mail in order to obtain further information on the reported vulnerability.
The User may contact Bubendorff to be informed of the progress made in resolving the vulnerability. In this respect, the User undertakes not to contact BUBENDORFF more than once every 30 calendar days, in order to allow the BUBENDORFF teams to make serene progress on the corrections to be deployed.
BUBENDORFF informs the User that the vulnerability has been fixed. The User is invited to confirm the resolution of the report sent.
When the software cannot be updated remotely, Bubendorff, through its customer service department, replaces the hardware affected by the vulnerability.
Once the correction has been published, the User may request that their vulnerability report be published. BUBENDORFF wishes to provide uniform advice to the Users concerned and requests the User at the origin of the disclosure to coordinate the public release with BUBENDORFF.
If a functional e-mail address is not provided, BUBENDORFF may not be able to process the report sent if it is incomplete or insufficiently informed, or to keep the User informed of the progress of the actions taken.
Report a vulnerability :
Any request that does not correspond to a vulnerability report will not be processed or transmitted.
For security reasons, we do not allow attachments to be sent at this stage. These can be sent to us when the vulnerability is processed.